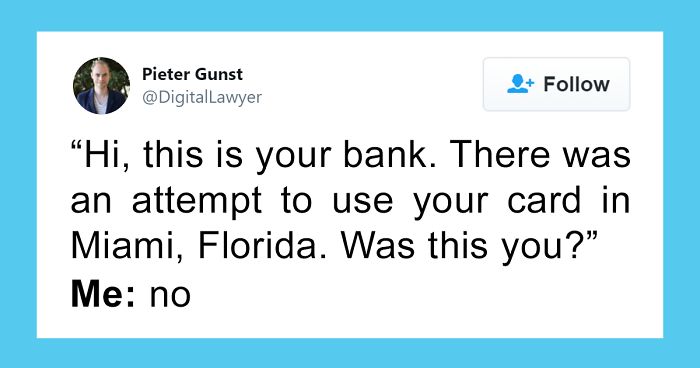
Scammers Have A New Way Of Tricking People Into Giving Them Their Credit Card Info, This Person Tells How To Recognize It
We like to think that we’re immune to scams. However, some of them are so advanced, they can trick even the most vigilant ones. Almost. Pieter Gunst, who has spent years working as a tech lawyer, recently tweeted how he nearly fell for a phishing attempt. Outlining the steps that almost fooled him, he pointed out what everyone should be constantly looking out for in order to keep themselves safe.
More info: Twitter
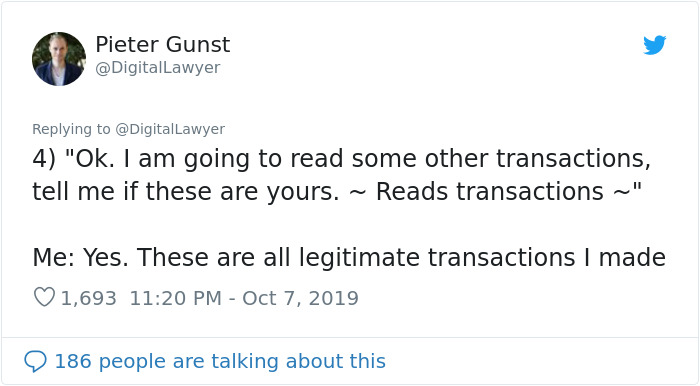
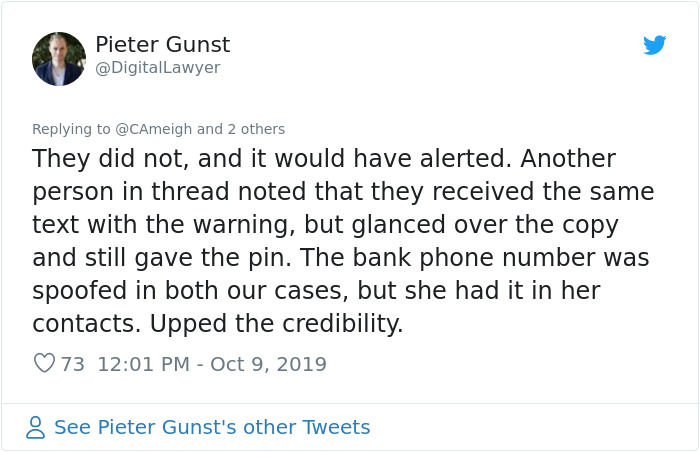
Image credits: DigitalLawyer
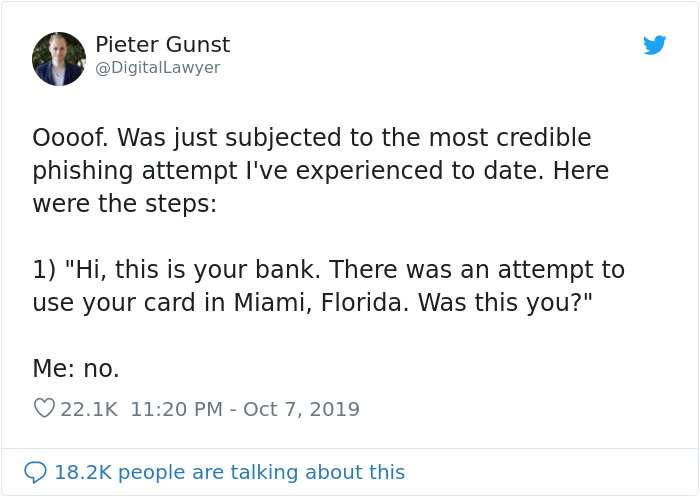
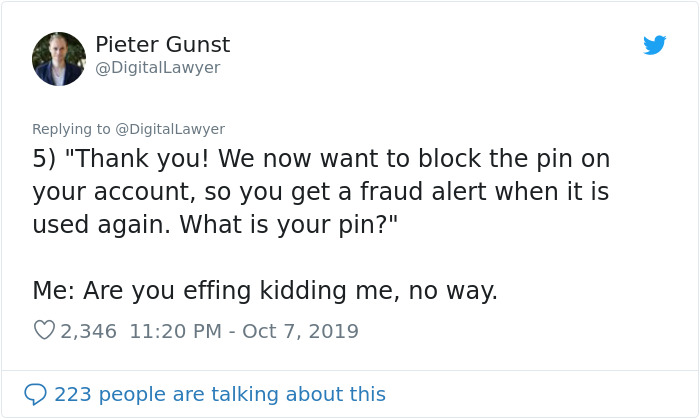
Image credits: DigitalLawyer
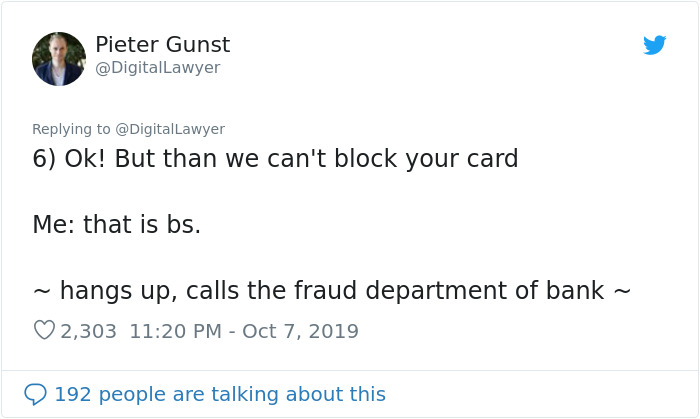
Image credits: DigitalLawyer
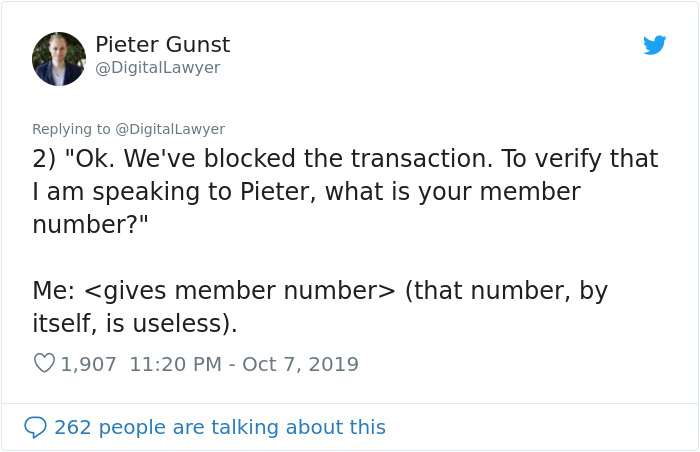
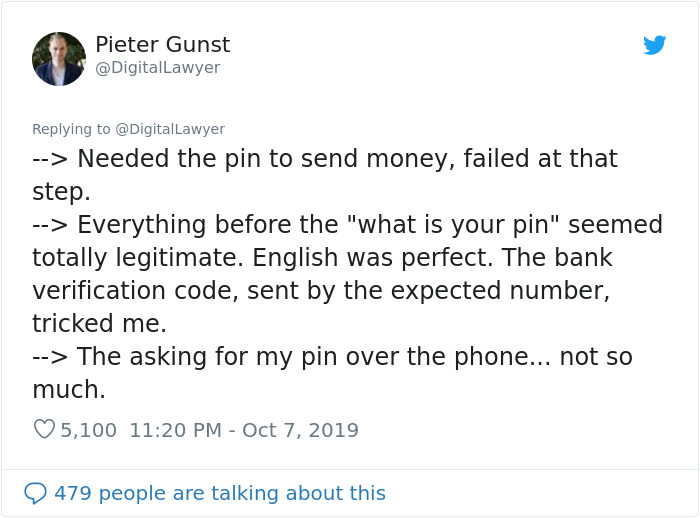
Image credits: DigitalLawyer
Image credits: DigitalLawyer
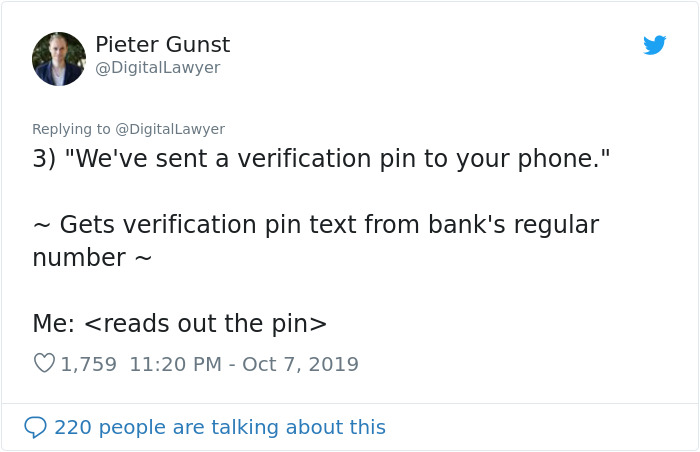
Image credits: DigitalLawyer
Image credits: DigitalLawyer
Image credits: DigitalLawyer
Image credits: DigitalLawyer
Microsoft’s security team constantly analyzes trends in cybersecurity threats. The company has been publishing Security Intelligence Reports at least annually since 2006, and they serve as an excellent indicator of these trends. The most recent report indicates that phishing attacks are now the most frequent threat to the cyber landscape, increasing 250% since the publication of the previous report.
To find out more about these illegal activities, Bored Panda spoke with Blue Bridge, a company that provides comprehensive IT services and solutions to large companies and public organizations, including data transmission and cybersecurity.
“Phishing is a method of social engineering, and it’s based on manipulating our emotions,” Blue Bridge cybersecurity expert Ugnius Klevinskas told Bored Panda. Klevinskas said that the reason why it’s so popular among scammers (and will continue to evolve) lies in human nature. “[We’re] curious and trustful, and, on the most part, aren’t ready to think critically in stressful situations.”
Klevinskas also pointed out the findings of various research, saying that neither age, nor education or profession contribute to one’s resistance to social engineering. “Anyone can fall for a similar scam,” he said. “Moreover, when it comes to this particular case, it’s worth highlighting that fake data was combined with the real one. Even though it wasn’t done in a very original manner, the execution was high-quality. It’s clear that the attack was well coordinated and the scammers had been prepared.”
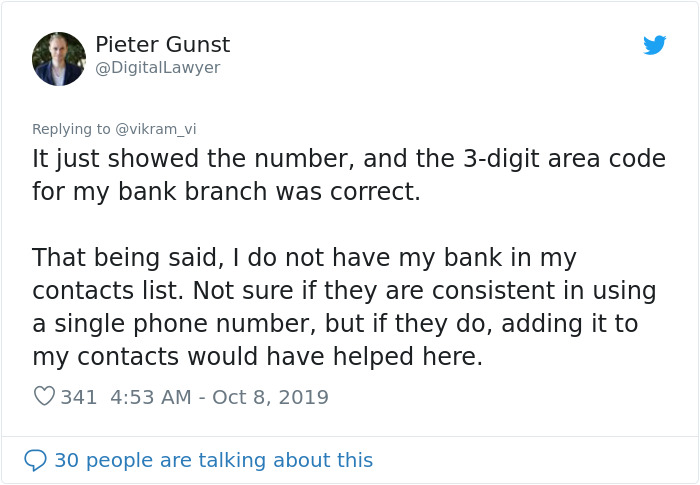
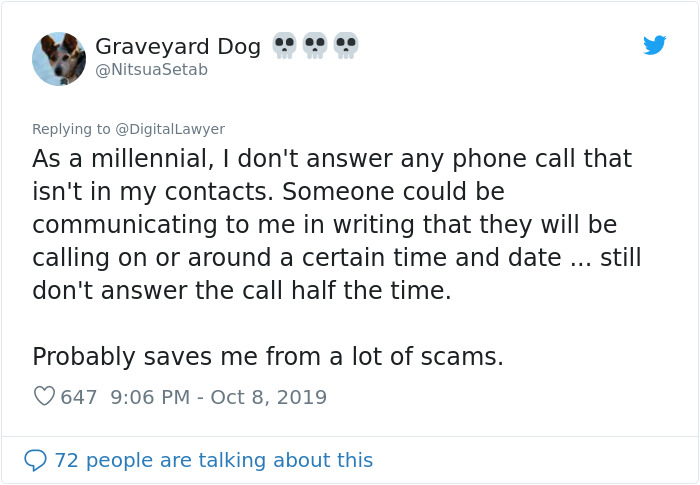
The expert also had some advice on how we all can protect ourselves from something like this: “If somebody asks you to disclose sensitive personal information, be it via e-mail, SMS or phone call, you have to stay vigilant,” Klevinskas said. “The best thing to do is to test the request through another channel. For example, if you received a suspicious e-mail, call the alleged organization or person who sent it and ask them about it. Or, let’s say, a bank employee phoned you, saying you have to provide them your PIN code or other similar info. In such a situation, you should end the conversation and call the bank yourself, making sure there actually is such a person working for that bank.”
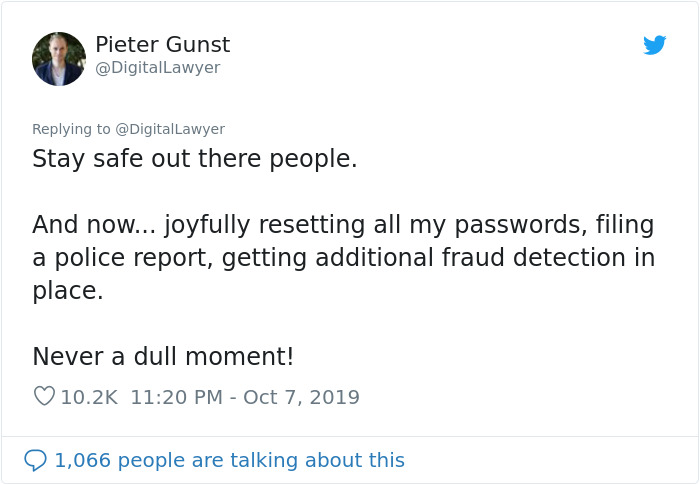
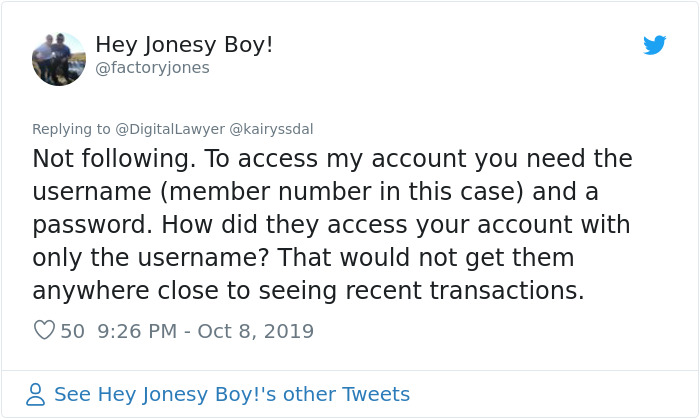
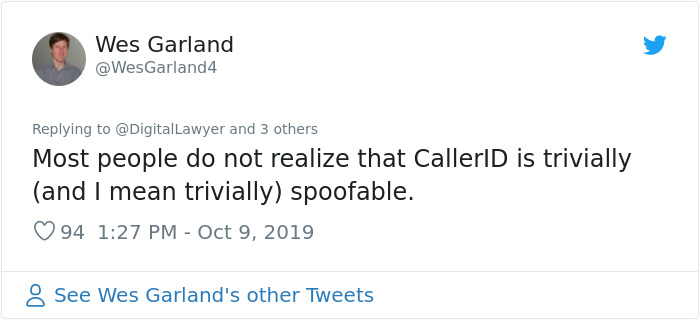
Some people asked Pieter to clarify a few things
Image credits: factoryjones
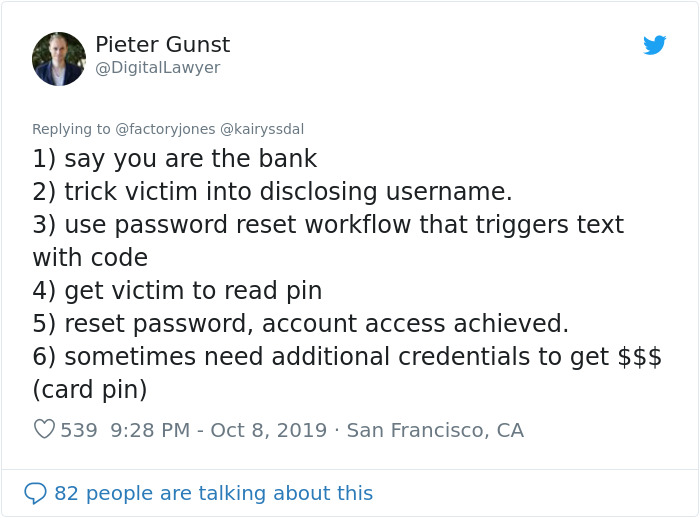
Which he happily did
Image credits: DigitalLawyer
Image credits: CAmeigh
Image credits: DigitalLawyer
Image credits: WesGarland4
Image credits: boink
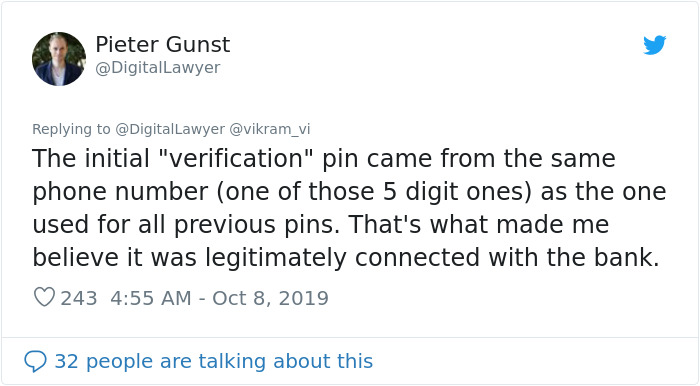
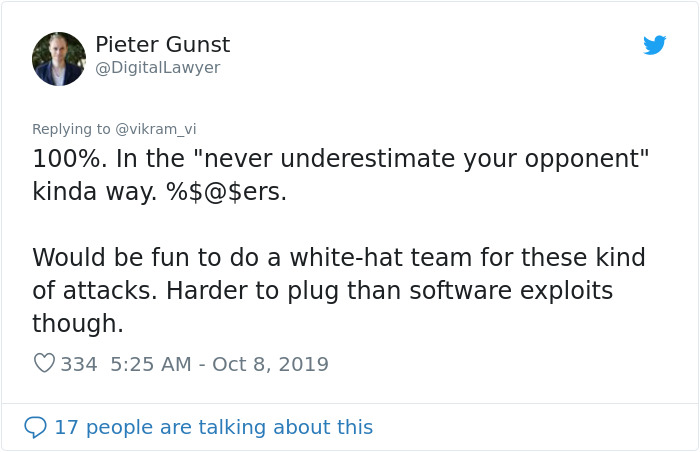
Image credits: vikram_vi
He then continued to explain the situation
Image credits: DigitalLawyer
Image credits: DigitalLawyer
Image credits: DigitalLawyer
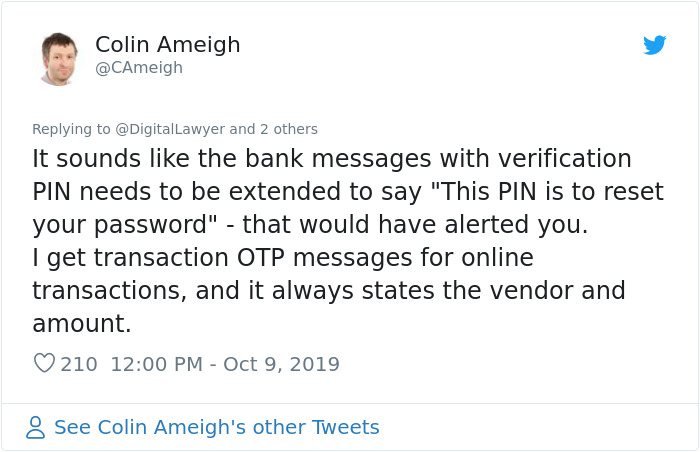
Here’s what others said about it
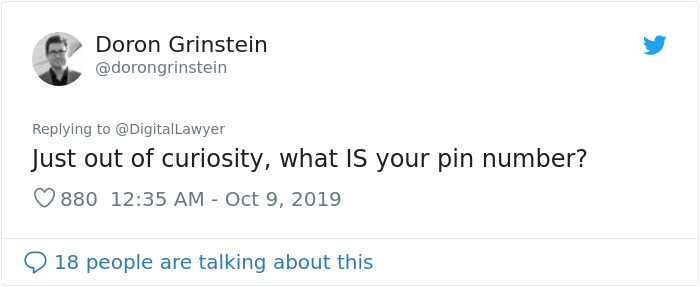
Image credits: dorongrinstein
Image credits: NitsuaSetab
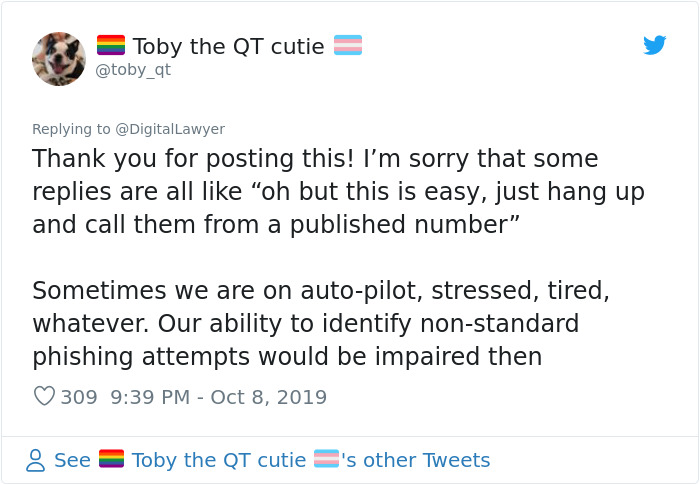
Image credits: toby_qt
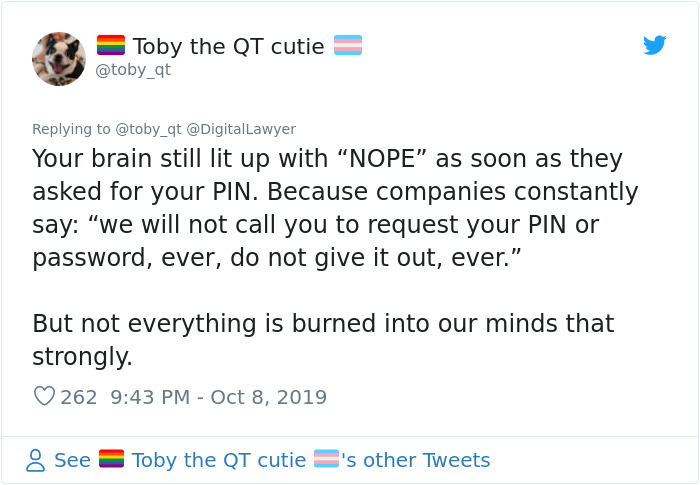
Image credits: toby_qt
exactly what I do anytime I get a call, text or email from "the bank".
Load More Replies...Most companies never call on that anyways. And for them asking for your pin number, they would already have that. I had fraudulant charges on my bank card and they never once called me about it. I found it looking at my statement and then alerted them to cover the charges.
My credit card company ALWAYS calls me when they detect unusual activity on my card and it has always proven to be the case. At one point someone in Egypt was using my card for long distance calls. One time when I lived in OH they called and asked me if I was making a bunch of small purchases all over FL. and I wasn't. So, I wouldn't have thought anything was strange until they asked for my PIN number either.
Load More Replies...if someone claiming to be your bank calls you and tries to get that sort of information, tell them you'll call the number on the back of your card and you will verify it that way.
Scary how they can send a text to your phone that looks like it is from your bank!! My bank always says that they will never contact me by phone about anything. I get alerts on my online banking if there is something urgent, otherwise everything is by post.
Actually, the guy is in front of his computer when he is calling you, When you give your member number, He is entering it, but instead of entering a password, He choose "reset password" and so a SMS is sent to your phone, with the new pin It's a real SMS coming from your bank. Nothing fake. So, of, course, he need this code to enter instead of you. In this story, he failed...
Load More Replies...What do you mean, "tricked me"? Every serious bank doesn't ask for any such information on the telephone or in emails so simple never ever give any bank details to somebody via phone or mail.
This guy is an idiot. If you get a call like that hang up. Then either call your bank back or go in to your local branch. This is common sense 101. How the hell did this guy get his own post on this? I never even affirm my identity in the positive over the phone. I ask who they are affiliated with, then I tell them I'm call back on the number I have for that company. If they are legit they never have a problem with it.
Right? The one time I had the bank contact me for suspicious activity it was an automated message that said to call the number on the back of my card. Banks KNOW they have told us never to give out information to anyone who calls us or call numbers back that are left for us. Official numbers only and go through the automated channel selection.
Load More Replies...Banks, police, and government related institutions, they usually don't call. Should they need anything from you, they will send an SMS or e-mail notification that might suggest to come in person, if it's something worth of your concern. Or they will send you an official written notice that will suggest you call them for more information. Anyway, anything serious is handled in person. Also, please, know that the banks are handling tons of accounts and they have no means and no staff to monitor every single account and its activities. Should there really occur a suspicious activity, you will be the one to notice, not them. They can only notice if it's a major hacker attack on their servers and then they will release an official notice to every member at once, or will publish it on their official website.
Until they do call. I had filled out a report for Social Security and didn't answer one question. I got a phone call from a number that looked to be from SSA and the woman left a message that I needed to return the call at thus and such number at East Coast times from 6 a.m. to 2 p.m., supposedly to accommodate West Coast callers. Sorry, I'm not getting up at 3 a.m. to call a scammer. I called the main SSA number and found out that the call was legit. When the lady called me again, she asked me for my SSN for "identity confirmation". I told her that I had thought that her call was a scam, especially with the weird working hours. She seemed annoyed that I even questioned the veracity of her call. We finished our business quickly and it was legitimate but it was a weird experience.
Load More Replies...Most fun I ever had was when a man with a thick East Indian accent called me to say he was from the IRS and I needed to pay my back taxes immediately or he would call the sheriff and have me arrested. I laughed. He says "You should not laugh. This is a serious matter." I said "I'm laughing because if you're the IRS..then I'm the Queen of England. Find a new gig, dude. The IRS never calls anyone. But I'm about to call the FBI." *click...Awe..he didn't wanna play no more....
I personally never even "almost" fall victim to these scams. I will just hang up and report those number to the FTC, bank, and complaint boards like http://whycall.me. However, what I think is some people who don't really familiar with the internet and these kind of information. They are way more vulnerable to these kind of scams. This is why we need to keep spreading the word, at least to our family.
The whole premise of the call is a big red flag. First off, you won’t be able to use your card, which will prompt you to call them, not the other way around. They will also fully identify themselves (name, bank department, etc) and give you a couple different ways to verify who you are. They will also be sitting in front of a computer that already has access to your account, so can see your transactions and identify the flagged unusual activity, with no need for you to give them your member/account number or PIN for them to see any of it. I live in Maryland, so the first time I had to fly to Nevada to put my father into a nursing home, my credit card was blocked not long after I started using it there. Calling customer service straightened it all out fairly quickly. Now, whenever I know I’m going to use the card for something unusual (travel or an unusually large purchase), I call and tell them to note on the account that I told them about it ahead of time.
What is a "member number"? I just have an account number and I would never recite it, or my PIN to so stranger over the phone. I Don't understand how that the scammer got that far. I wouldn't work with my bank. And if I got a call from my bank, I'd say "I'll be right over" since it's only two streets away.
I think....take your parents advice..."NEVER TALK TO STRANGERS"! Do not waste time communicating with a random caller. Phone your bank from a different phone than the one you were contacted on and report incident.
Me: But I don't have an account with Your Bank. I have an account with My Bank...
I never get calls from my bank. And I would immediately be suspicious of a call that purports to be from my bank. Member / account number to verify- no way. Seriously, it is as bad as the calls that claim to be from Microsoft. I still get those and I still hang up on them.
If you are Australian this is the government site anti all scams advice.https://www.staysmartonline.gov.au/
And I don't answer the phone unless I see it is someone I know. If it is real they can leave a message. Even then I had someone pretending to be the phone company cutting of my net. To stop this happening send credit card details to....
Load More Replies...Or just tell the caller "I don't have a card/account with you," and hang up. Works for me.
it would be impossible to scam me, only 300'000 people speaks my native language and my bank too
I never accept calls on the phone unless I am expecting the call beforehand. I don't care if its the bank, the police, or someone else. If they need to speak with me, they can contact me another way (like the police) or wait until I contact them directly (like the bank). Also, I keep a balance sheet listing my transactions and incomes. So I always know what I've done or not done. If I seem something that doesn't track, then I will call the bank on it no matter what. So if the "bank" is calling me, I can just ignore it then call the bank bank to make sure it's them.
It's funny because just to get someone to talk to you on the banks phone they need a bunch of info which I understand but there should also be something that only you and whoever's reading the screen in front of them like a key word/phrase! Oh also sir you are the best at golf! Sort of thing or you have great art skills something stupid no one else would thing of so that if they call and don't say that you no long say anything and hang up! And I mean right after the important stuff like thanks for answering my questions Mr. prince is great!
I didn't answer or reply to a phone number I didn't recognise. Turned out to be Amazon delivery driver trying to work out where my house was (it is a bit tricky to find). So, just meant my parcel was a day late. I'd rather have that than a dodgy phone call
My husband, who has concussive dementia got caught in this exact same scam, just a month ago. My daughter, who works with the police, walked in mid call and told him "hang up now", she realized what was happening and was able to stop it. Still had to cancel everything because they had tricked an old man with dementia into giving them certain information. Those people are the scum of the earth and we have a new house rule, that I am the only one who speaks with the bank and credit card companies. if they call.
I don't do any financial transactions on my phone. NONE. My bank info isn't on there either. My spouse suffered a scam on his phone through Apple.
One thing I don't get: They asked fro the account number, then started the actual password reset at the person's bank. How did they know which bank? Can they identify the bank from the account number? Do they try the same account number at 20 different bank's password reset sites?
first 3 digits of the account number are called the protocol number, and indicate the bank the account belongs to.
Load More Replies...I work for a skip-tracing company that 15 years ago had the capability to spoof a phone number. It's not difficult.
exactly what I do anytime I get a call, text or email from "the bank".
Load More Replies...Most companies never call on that anyways. And for them asking for your pin number, they would already have that. I had fraudulant charges on my bank card and they never once called me about it. I found it looking at my statement and then alerted them to cover the charges.
My credit card company ALWAYS calls me when they detect unusual activity on my card and it has always proven to be the case. At one point someone in Egypt was using my card for long distance calls. One time when I lived in OH they called and asked me if I was making a bunch of small purchases all over FL. and I wasn't. So, I wouldn't have thought anything was strange until they asked for my PIN number either.
Load More Replies...if someone claiming to be your bank calls you and tries to get that sort of information, tell them you'll call the number on the back of your card and you will verify it that way.
Scary how they can send a text to your phone that looks like it is from your bank!! My bank always says that they will never contact me by phone about anything. I get alerts on my online banking if there is something urgent, otherwise everything is by post.
Actually, the guy is in front of his computer when he is calling you, When you give your member number, He is entering it, but instead of entering a password, He choose "reset password" and so a SMS is sent to your phone, with the new pin It's a real SMS coming from your bank. Nothing fake. So, of, course, he need this code to enter instead of you. In this story, he failed...
Load More Replies...What do you mean, "tricked me"? Every serious bank doesn't ask for any such information on the telephone or in emails so simple never ever give any bank details to somebody via phone or mail.
This guy is an idiot. If you get a call like that hang up. Then either call your bank back or go in to your local branch. This is common sense 101. How the hell did this guy get his own post on this? I never even affirm my identity in the positive over the phone. I ask who they are affiliated with, then I tell them I'm call back on the number I have for that company. If they are legit they never have a problem with it.
Right? The one time I had the bank contact me for suspicious activity it was an automated message that said to call the number on the back of my card. Banks KNOW they have told us never to give out information to anyone who calls us or call numbers back that are left for us. Official numbers only and go through the automated channel selection.
Load More Replies...Banks, police, and government related institutions, they usually don't call. Should they need anything from you, they will send an SMS or e-mail notification that might suggest to come in person, if it's something worth of your concern. Or they will send you an official written notice that will suggest you call them for more information. Anyway, anything serious is handled in person. Also, please, know that the banks are handling tons of accounts and they have no means and no staff to monitor every single account and its activities. Should there really occur a suspicious activity, you will be the one to notice, not them. They can only notice if it's a major hacker attack on their servers and then they will release an official notice to every member at once, or will publish it on their official website.
Until they do call. I had filled out a report for Social Security and didn't answer one question. I got a phone call from a number that looked to be from SSA and the woman left a message that I needed to return the call at thus and such number at East Coast times from 6 a.m. to 2 p.m., supposedly to accommodate West Coast callers. Sorry, I'm not getting up at 3 a.m. to call a scammer. I called the main SSA number and found out that the call was legit. When the lady called me again, she asked me for my SSN for "identity confirmation". I told her that I had thought that her call was a scam, especially with the weird working hours. She seemed annoyed that I even questioned the veracity of her call. We finished our business quickly and it was legitimate but it was a weird experience.
Load More Replies...Most fun I ever had was when a man with a thick East Indian accent called me to say he was from the IRS and I needed to pay my back taxes immediately or he would call the sheriff and have me arrested. I laughed. He says "You should not laugh. This is a serious matter." I said "I'm laughing because if you're the IRS..then I'm the Queen of England. Find a new gig, dude. The IRS never calls anyone. But I'm about to call the FBI." *click...Awe..he didn't wanna play no more....
I personally never even "almost" fall victim to these scams. I will just hang up and report those number to the FTC, bank, and complaint boards like http://whycall.me. However, what I think is some people who don't really familiar with the internet and these kind of information. They are way more vulnerable to these kind of scams. This is why we need to keep spreading the word, at least to our family.
The whole premise of the call is a big red flag. First off, you won’t be able to use your card, which will prompt you to call them, not the other way around. They will also fully identify themselves (name, bank department, etc) and give you a couple different ways to verify who you are. They will also be sitting in front of a computer that already has access to your account, so can see your transactions and identify the flagged unusual activity, with no need for you to give them your member/account number or PIN for them to see any of it. I live in Maryland, so the first time I had to fly to Nevada to put my father into a nursing home, my credit card was blocked not long after I started using it there. Calling customer service straightened it all out fairly quickly. Now, whenever I know I’m going to use the card for something unusual (travel or an unusually large purchase), I call and tell them to note on the account that I told them about it ahead of time.
What is a "member number"? I just have an account number and I would never recite it, or my PIN to so stranger over the phone. I Don't understand how that the scammer got that far. I wouldn't work with my bank. And if I got a call from my bank, I'd say "I'll be right over" since it's only two streets away.
I think....take your parents advice..."NEVER TALK TO STRANGERS"! Do not waste time communicating with a random caller. Phone your bank from a different phone than the one you were contacted on and report incident.
Me: But I don't have an account with Your Bank. I have an account with My Bank...
I never get calls from my bank. And I would immediately be suspicious of a call that purports to be from my bank. Member / account number to verify- no way. Seriously, it is as bad as the calls that claim to be from Microsoft. I still get those and I still hang up on them.
If you are Australian this is the government site anti all scams advice.https://www.staysmartonline.gov.au/
And I don't answer the phone unless I see it is someone I know. If it is real they can leave a message. Even then I had someone pretending to be the phone company cutting of my net. To stop this happening send credit card details to....
Load More Replies...Or just tell the caller "I don't have a card/account with you," and hang up. Works for me.
it would be impossible to scam me, only 300'000 people speaks my native language and my bank too
I never accept calls on the phone unless I am expecting the call beforehand. I don't care if its the bank, the police, or someone else. If they need to speak with me, they can contact me another way (like the police) or wait until I contact them directly (like the bank). Also, I keep a balance sheet listing my transactions and incomes. So I always know what I've done or not done. If I seem something that doesn't track, then I will call the bank on it no matter what. So if the "bank" is calling me, I can just ignore it then call the bank bank to make sure it's them.
It's funny because just to get someone to talk to you on the banks phone they need a bunch of info which I understand but there should also be something that only you and whoever's reading the screen in front of them like a key word/phrase! Oh also sir you are the best at golf! Sort of thing or you have great art skills something stupid no one else would thing of so that if they call and don't say that you no long say anything and hang up! And I mean right after the important stuff like thanks for answering my questions Mr. prince is great!
I didn't answer or reply to a phone number I didn't recognise. Turned out to be Amazon delivery driver trying to work out where my house was (it is a bit tricky to find). So, just meant my parcel was a day late. I'd rather have that than a dodgy phone call
My husband, who has concussive dementia got caught in this exact same scam, just a month ago. My daughter, who works with the police, walked in mid call and told him "hang up now", she realized what was happening and was able to stop it. Still had to cancel everything because they had tricked an old man with dementia into giving them certain information. Those people are the scum of the earth and we have a new house rule, that I am the only one who speaks with the bank and credit card companies. if they call.
I don't do any financial transactions on my phone. NONE. My bank info isn't on there either. My spouse suffered a scam on his phone through Apple.
One thing I don't get: They asked fro the account number, then started the actual password reset at the person's bank. How did they know which bank? Can they identify the bank from the account number? Do they try the same account number at 20 different bank's password reset sites?
first 3 digits of the account number are called the protocol number, and indicate the bank the account belongs to.
Load More Replies...I work for a skip-tracing company that 15 years ago had the capability to spoof a phone number. It's not difficult.





212
54